The year is 2025 (or it's about to be). That's a fake year. That's a year that should only exist on moonbases and undersea colonies. Frankly it's offensive that it's 2025 and the only science fiction dream that came true was a plutocracy killing the planet.
Oh, and hacking is a job you can have.
Well, maybe.
Don't feel like reading? Jump to Solutions.
Embrace Reality
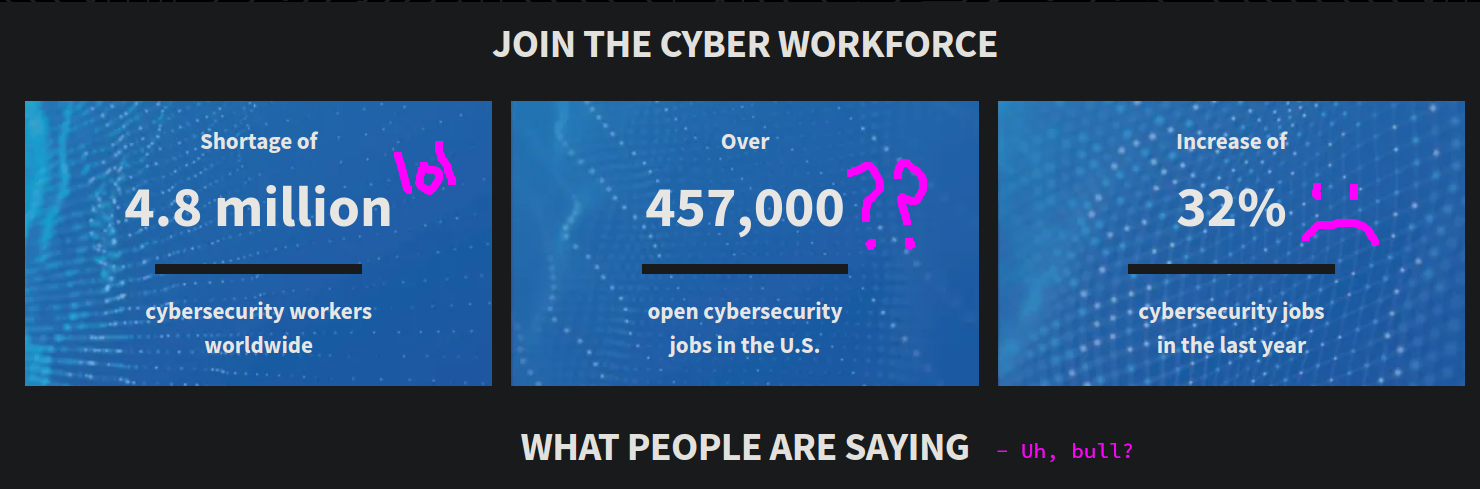
These are...probably nonsense.
While CISA would like you to believe there are nearly half a million open cybersecurity jobs in the Unites States alone, that number is bogus, created by a firm that sells cybersecurity certification training. I don't know how many open cyber jobs there are, but it ain't that. I don't even think it's within the same order of magnitude.
Unfortunately, the US government, especially the Biden Administration, has committed to this fiction. We don't make it two paragraphs into the the keystone National Cyber Workforce and Education Strategy (NCWES) before the jobs number is dropped:
There are structural challenges to building our cyber workforce and education system: hundreds of thousands of vacant cyber jobs; an insufficiently diverse workforce to fill those jobs; and barriers to accessing cyber education and training. The National Cyber Workforce and Education Strategy charts a path to resolving these challenges by working towards filling cyber jobs for working families.
The term "jobs" appears 40 times in that document, usually alongside descriptors like "quality," or "good-paying." This is the sell: cyber is a work guarantee for the White House, a way to promise work for those who have found themselves out of work for all the reasons America always leaves people out of work.
Here's the thing about job retraining programs: they don't work. They especially don't work when employers can find higher skilled labor cheaper overseas. In the realm of technology, there isn't even a logistical cost.
So no, the White House isn't going to get you a cybersecurity job. And there aren't that many to begin with.
Ask anyone who's been applying to jobs—including experienced, credentialed folks. It's rough out there. While I don't know if I would go as far as this author, the sentiments in Cybersecurity is full! ring true. In particular, many (including myself) have encountered the phenomenon of "ghost jobs," listings that look promising, but are hosted by employers who are not actively hiring. They just leave the bait on the hook to motivate applicants to keep applying (and keep paying for training). One UK study found that as many as 46% of lob listings may be spectral.
There are some claims that the market has peaked, or that the true demand has always been much lower. Part of the problem is that the folks creating the statistics on open roles, are almost always the ones selling you training, and have a vested interested in convincing aspirants they have a shot—but only with their certification.
So listen. It's rough out there, rougher than anyone wants to admit. And that is in the cybersecurity jobs market as a whole, to say nothing of the rarefied "offensive security" positions.
I Don't Mean to Be Offensive
Wanna be a red teamer? A pentester? A hoodie-wearing, lockpick-carrying, exploit-slinging good-guy-doing-bad-guy-stuff? Cool. Get in line.
I'm going to tell you the truth, because you need to hear the truth. Locking yourself into chasing only "offensive" positions is a great way to never get hired. Odds are, you won't be able to start there. You may never get there at all. There just aren't enough positions for all the people who want to pop shells and break into buildings—especially at the entry level.
I know for a fact just how many people want to be offensive security professionals—or at least think they do. TTI's single red team course is our most popular. As it happens, it is also the least completed as a percentage of enrollees. Perhaps that's because the course is not about popping shells, but rather the ethics and professionalism necessary to succeed in the role. Put another way, it's about the reality of the job, not CTF challenges or bug bounties.
If you're not willing to put in the time to complete a short course on that reality, you may not be cut out for offensive cybersecurity. Well, any cybersecurity really, but definitely a role that demands true integrity—doing right when nobody can see you.
But even if you're willing to put in all the time and effort to train up on these skills, the scarcity of positions remains a reality. Be real about that. It's fine to want to be a pentester or a red teamer. It is also fine to do something else because you need to.
Don't Get Defensive, Now
So let's talk about where there are some jobs—at least in theory. The defensive aspect of cybersecurity tends to have more available positions. Many of these, however, are entry-level SOC (Security Operations Center) Analyst positions that are certainly not the "well-paying jobs" the White House would want you to believe they are.
And SOC work is, I'm sorry to say, deeply unsexy. You're receiving alerts from tools like endpoint detection software, then determining whether it merits escalation, potentially performing additional analysis, or (more likely) escalating the ticket to seniors who will perform the investigation. This is not the only kind of defensive cyber job available, but it's the closest to what I would describe as "entry-level." Everything else requires a measure of experience and technical proficiency for success. That's not to say SOC analysts lack technical skills—far from it! The best analysts I know are the ones who bring systems understanding to their evaluation of incoming alerts and log data. But at the lower rungs of the analyst echelon, it can be possible to get by without much prior IT experience, supported by a scaffolding of process and institutional knowledge that brings you up to speed.
As for the rest of defensive cybersecurity, from Compliance roles to Incident Response to Security Engineering, here comes the part you're gonna hate:
You can't jump in without prior IT experience. Anyone who tells you otherwise is selling something, and it isn't your success.
Security is a Specialization
Security Skills Tree from the amazing MakerSkillTree project.
I've been doing pure IT security work for a while now, and I still feel like I'm just a system administrator on special work detail—or software developer, depending on the day. I have developed specialized skills for threat hunting, forensics, incident response, and yes, pentesting/ red team operations as needed (oh, the joys of being a purple teamer!). But on a day-to-day basis, the skills I rely on and that provide value to my team are core competencies in:
- Linux/Windows system administration
- Network engineering
- Software design and architecture
These are skills that I've accrued over a career doing it all in IT. I've made my own network cable, connected it to patch panels and switches I've configured myself. I've deployed fleets of laptops; I've maintained websites; I've developed applications for real people. The double-edged sword of working in K-12 IT is that, since nobody else is around to help you, you gain a dizzying breadth of experience. I'm grateful for that background as a security researcher, because I know how the systems I protect actually work. I know how the people I work with think, what they prioritize, and how to make security matter to them.
Cybersecurity is a specialization of IT. It's a niche lateral move that requires understanding of the rest of IT to function. It is not a parallel "industry," no matter how much that term is thrown around, and it is most certainly not a position superior to other IT. Indeed, security serves the rest of IT; we empower and enable systems to do their jobs. The most secure system is off, disconnected from networks. That's also a useless system. If you're thinking of security as a promotion of sorts, you're in for a world of hurt. It may pay better than other IT jobs, but that does not come with magic authority over your colleagues. The moment you forget it's a service role, you fail.
Solutions
So you wanna get into cybersecurity in 2025? Truly, I wish you all the best. But if you're entering the field without a background in IT, you're going to have a devil of a time—not just applying for open positions, but even grasping the true nature of the work. Consider that beginning in another component of IT, like working desktop support, is not "beneath" you. On the contrary, those support roles are where you learn the reality of deploying systems into human hands. You learn how non-technical users think and treat their devices. It's an invaluable experience, and it pays much better than spending day after day applying to ghost jobs.
I'd also strongly recommend building some experience with system administration. We need Linux and Windows admins more than we need security specialists. And once you begin the operations journey, moving laterally to security is much easier than starting from scratch. That's why the courses at The Taggart Institute focus so heavily on the fundamental skills, rather than specializing too much on niche security topics. The core skills get you in the door—maybe not the one you intended, but it's much easier to move between rooms once you're inside.
Not for nothing, but The Homelab Almanac provides a roadmap for building an environment to develop your administration skills as well as your security skills. I might also check out A Cloud Guru from Pluralsight, if you can afford it. They're about as good a training platform as I know of for administration skills, and more.
You wanna do cybersecurity in 2025? I hope you get the chance. But I want to see you gainfully employed even more. I implore you to consider starting elsewhere in your journey, building the skills we need in the field, and applying for jobs that are actually open, rather than expending all your energy and time chasing ghosts.
