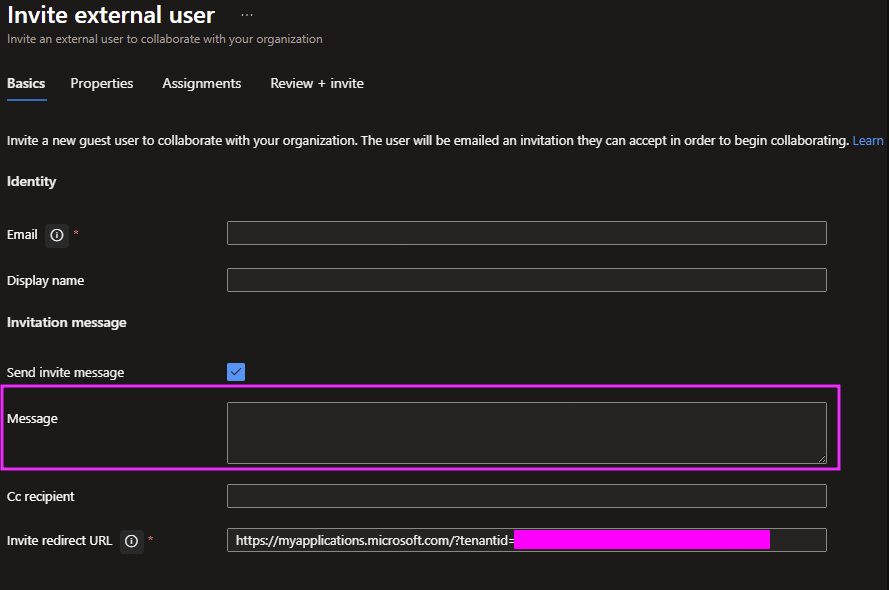
We have identified a new phishing/reverse phishing campaign that uses Microsoft Entra tenant invitations to trick recipients into calling a telephone number, referencing a fictitious bill. From the phone number, normal TOAD TTPs are in play. The use of Entra Guest user invitations seems solely to take advantage of the Message field in the Guest User invitation.
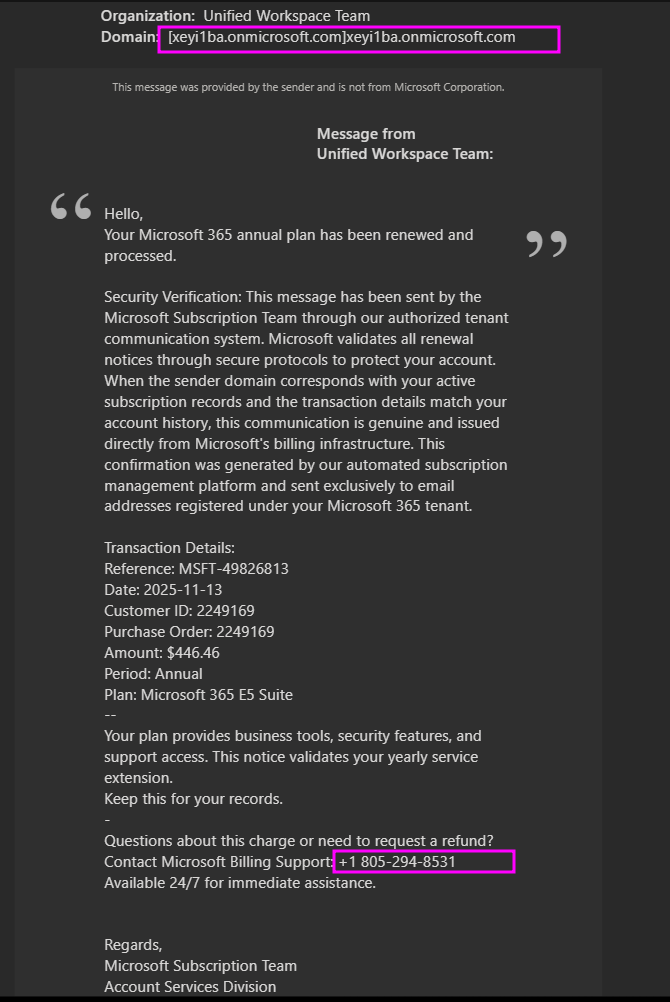
This field can be arbitrarily long, and is used to create a phishing lure.
Invites will come from invites@microsoft[.]com, which is a legitimate address and likely won't be blocked by email filters. This is similar to previous campaigns that use message fields in notifications from trusted services to embed a phishing lure.
Recommended Actions
If you have access to email logs, I recommend searching for listed strings below.
IoCs
| Indicator | Type | Description |
|---|---|---|
invites@microsoft[.]com | Sender address for Entra invites | |
invited you to access applications within their organization | String | Email Subject substring to search for Guest User invitations |
CloudSync | String | Attacker Tenant Name |
Advanced Suite Services | String | Attacker Tenant Name |
TenantHub | String | Attacker Tenant Name |
Unified Workspace Team | String | Attacker Tenant Name |
Advanced Suite Services | String | Attacker Tenant Name |
x44xfqf.onmicrosoft[.]com | Domain | Attacker Tenant Domain |
woodedlif.onmicrosoft[.]com | Domain | Attacker Tenant Domain |
xeyi1ba.onmicrosoft[.]com | Domain | Attacker Tenant Domain |
x44xfgf.onmicrosoft[.]com | Domain | Attacker Tenant Domain |
18052948531 | Telephone Number | Listed Number in observed lures |
Acknowledgments
Thanks to Ian Campbell and cr0w for additional corroboration on this campaign.